In the quest for a good solution to allow different groups to control their own content on a WordPress site, I came across the Advanced Access Manager plugin. During a standard cursory investigation of the code I discovered that any logged in user could execute any of the AJAX actions without proper authorization.
As a normal subscriber account, I was able to give myself administrator privileges on the site and do much more.
The wordpress.org repository claims there are 50,000+ active installs of this plugin. If you are using a version <= 3.2.1, upgrade immediately.
Nonce Leak
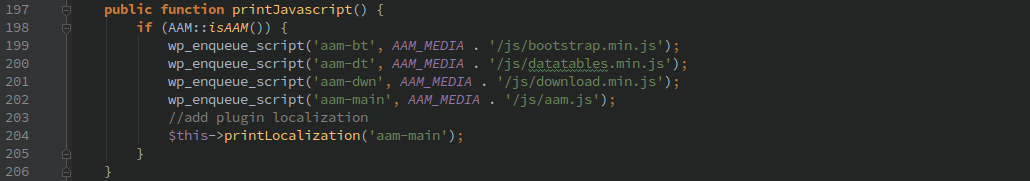
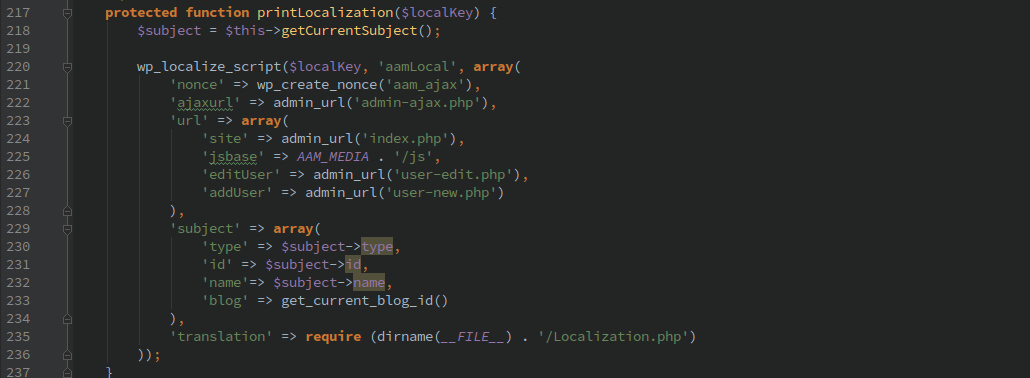
The AJAX actions were protected only with the ‘aam_ajax’ nonce which could be leaked by passing in HTTP POST variable ‘action=aam’. The following function is called from the ‘admin_print_scripts’ action, which in turn calls the printLocalization() function which includes the nonce.
Unrestricted AJAX Actions
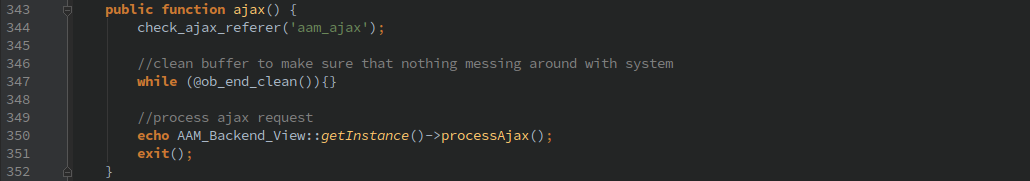
Once you have acquired a valid nonce, as a logged in user you can then call the ‘aam’ AJAX action.
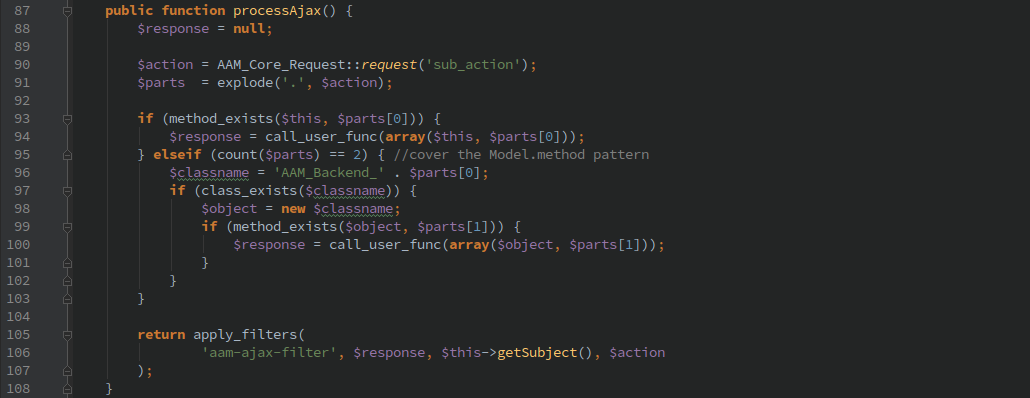
Which will allow you to call any function in the ‘AAM_Backend_View’ class or in any class that begins with ‘AAM_Backend_’
Almost every action taken by this plugin goes through this function, so anything that an administrator can do is now accessible to anyone with basic login credentials.
Timeline
- 5/11/2016 8:25pm Submitted contact form for initial contact
- 5/12/2016 5:34am Response received
- 5/12/2016 8:10am Initial Disclosure
- 6/15/2016 GitHub repository updated
- 6/20/2016 Version 3.2.2 released