Shortcode Injection Vulnerability
Ultimate Member versions older than 1.3.84 allow unauthenticated users to execute arbitrary WordPress shortcodes via AJAX. The vulnerable code exists as far back as version 1.0.0 when the plugin was first published. If you are using any version of this plugin, update immediately. At this time, the plugin revision notes do not address this vulnerability nor has the developer released any information related to this issue.
The default WordPress shortcodes are relatively secure but other installed plugins often include insecure shortcodes, including the Ultimate Member plugin. Some of the Ultimate Member shortcodes are documented at http://docs.ultimatemember.com/article/210-ultimate-member-shortcodes.
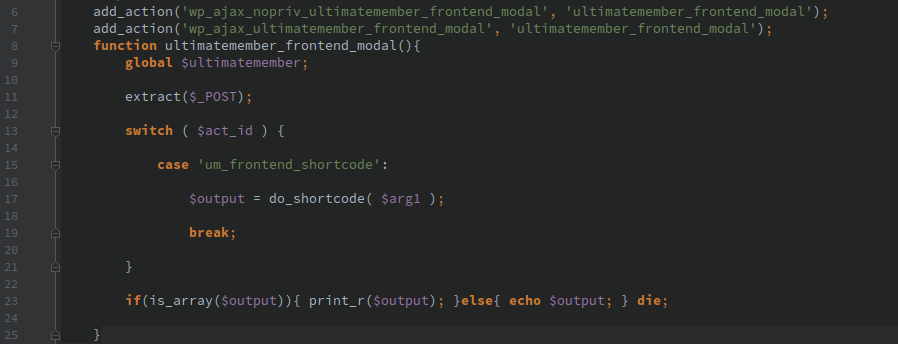
Executing arbitrary shortcodes
Ultimate Member adds the ‘ultimatemember_frontend_modal’ AJAX action which is accessible to anyone whether they are logged in or not. This allows passing arbitrary arguments to the do_shortcode() function and returns the results.
Include arbitrary PHP files
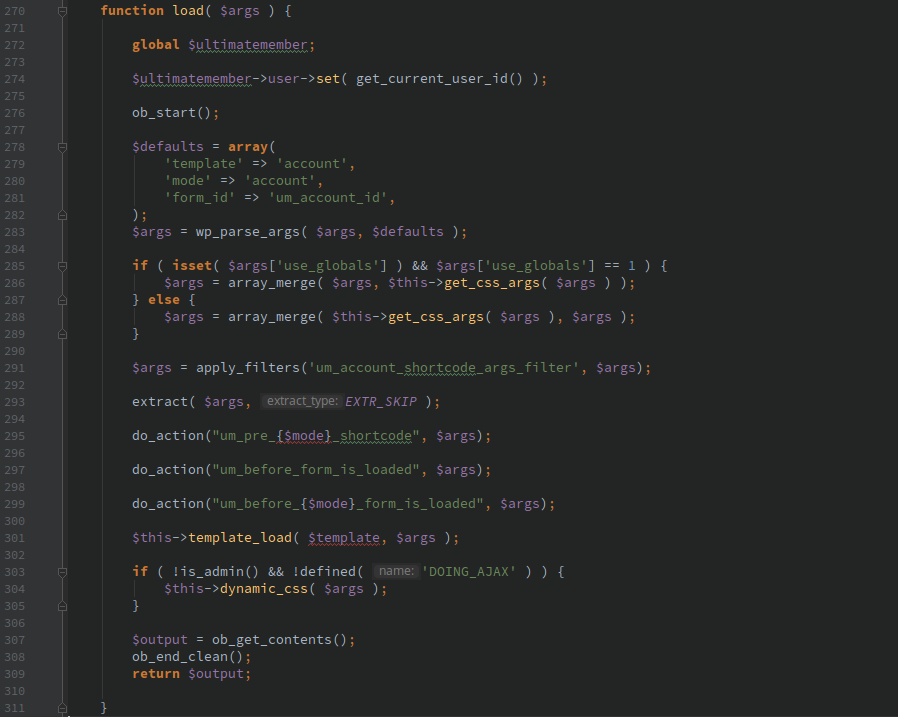
Using directory traversal and the ‘ultimatemember_account’ shortcode PHP files accessible on the host can be included. The following function is what is called when the ‘ultimatemember_account’ shortcode is executed.
Adding a template argument to the shortcode allows the PHP file to be included.
For example the following shortcode call allows viewing some user stats from the dashboard:
[ultimatemember_account template=../admin/templates/dashboard/users]
If a method could be discovered that allows uploading arbitrary PHP code, this could be used to execute that code.
Timeline
- 2/27/2017 Notified developer of issue
- 3/9/2017 Second notification to developer
- 3/10/2017 ‘Clean up’ commit on GitHub
- 3/10/2017 Developer reply saying they removed the offending code
- 4/17/2017 5:30AM PST Version 1.3.84 tagged in GitHub
- 4/17/2017 6:34PM PST Version 1.3.84 released on wordpress.org