Sprout Invoices is a WordPress plugin for creating invoices from Sprout Apps. This is another low use plugin (1,000+ active installs on the free version as reported by the wordpress.org stats page). I believe that any issues related to an invoice/payment system need to be reported so people can get them updated before it hits them in the bank account.
Unauthenticated access to methods named init
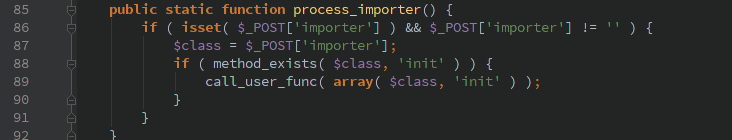
Inside controllers/importers/Importer.php the class hooks into the ‘init’ WordPress action to provide access to various importer modules (ironically enough one of them is for the WP-Invoice package that I recently posted about). This setup allows an unauthenticated user to pass in the classname that is used to call the function ‘init’
I don’t know of any classes that come with a default WordPress install that are readily exploitable, but there could be other plugins/themes installed that could be easily exploited by being able to call their function by an arbitrary user.
Unauthenticated uploading of CSV files
The CSV import module allows an unauthenticated user to upload CSV files, though it will not actually import without a valid nonce that does not appear to be leaked without having proper permissions. A malicious user could upload large files to attempt to fill up the storage space, though with the high limits available today it’s probably unlikely.
Unauthenticated access to unreleased JSON API
Dan Cameron, the developer, said that JSON API included was in development but abandoned in favor of the official WordPress REST API. Though in this release it was enabled and fully accessible to anyone without being logged in. At first glance it looks like there is some code to authenticate requests that contain ‘create-‘, but as long as that string is not included in $_REQUEST[‘si_json_api’] then it will pass along.
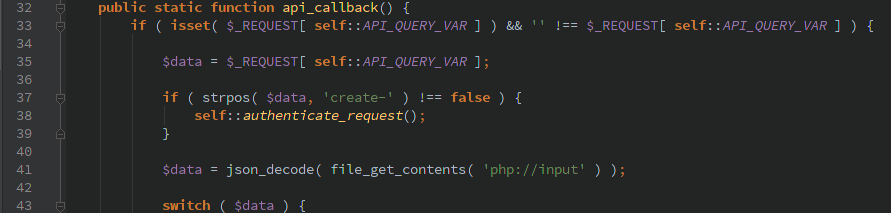
After the possible authentication function, php://input is read and passed to json_decode so any of the available API functions can be used which would allow you to create/view: clients, payments, estimates, and invoices.
Timeline
- 1/15/2016 12:42am Initial contact form submitted
- 1/15/2016 1:35pm Response from developer
- 1/15/2016 5:01pm Full disclosure sent to developer
- 1/18/2016 New version released

