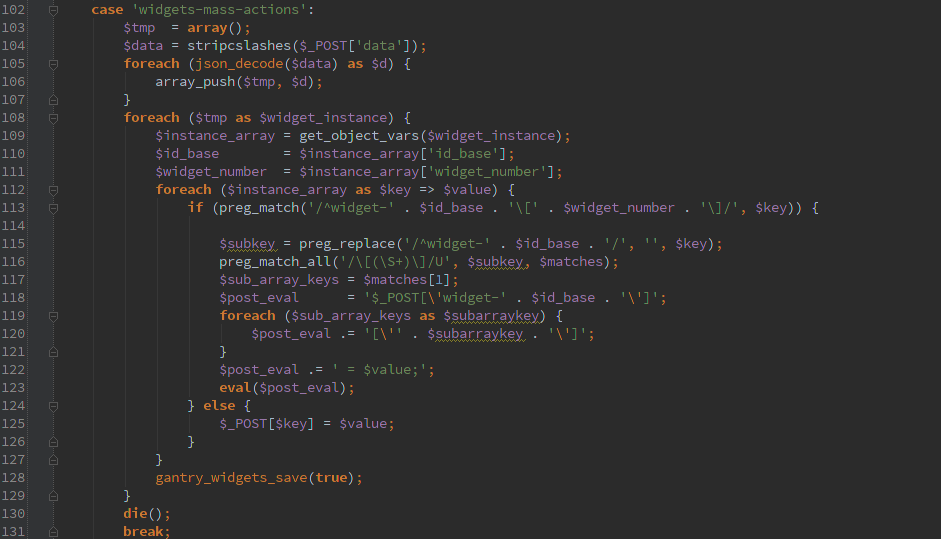
I noticed a minor potential security vulnerability in the Gantry Web Theme Framework for WordPress. This allows arbitrary code to be executed remotely, fortunately it requires a WordPress account (does not have to be admin) and also requires some crafty building of JSON text to pass through.
By POSTing an AJAX request with action=gantry_admin&gantry_action=widgets-mass-actions you can get into this chunk of code.
It took some really complicated building of the $_POST[‘data’] JSON to get all of the quotes balanced, but it is possible to get that code executed by eval().
All of the other AJAX functions appear to check a nonce and current_user_can() so they are secure, this function initially pushed this authorization into the gantry_widgets_save() function which would get called after the JSON is decoded.
The lesson here is to always do your authorization as early as possible.
Timeline
- 3/4/2015 Sent request via web form with details
- 3/5/2015 2:26am Response received saying details forwarded to development team
- 3/10/2015 Updated version released