Yesterday I noticed this tweet from IgnitionDeck 
I’d never heard of them before so I decided to take a quick look at their page and see what code was available to look at. They have several paid plugins but also a free plugin on wordpress.org.
I spent a couple minutes looking at the code while I was eating breakfast. Right away I noticed a couple of issues and sent off an email. They were quick to respond and within a few hours had released an update version.
Analysis
One of the first things I search for is AJAX handlers, often developers forget to verify if the user is actually allowed to do the action especially if the page that links to the action is behind an admin interface that requires a login.
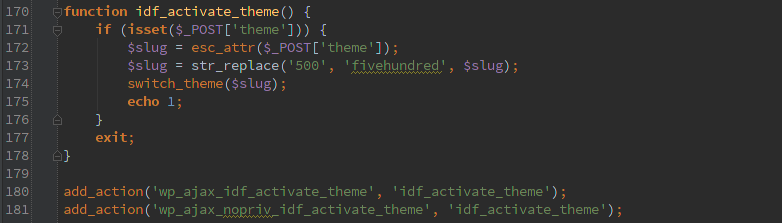
Here a simple POST lets an un-authenticated user change the active theme.
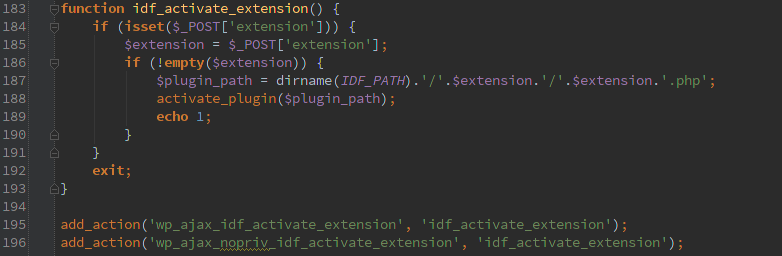
This one lets an un-authenticated user activate an installed plugin. Right away I thought some directory traversal would be fun, but since the same variable is used for the directory and filename it won’t work.
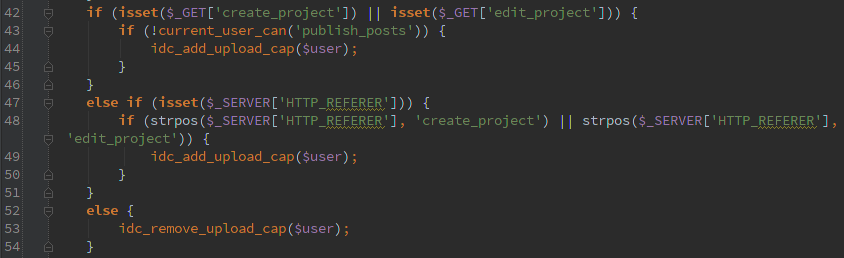
Next up I noticed a function that runs during the ‘init’ action that acts on user input.
If ‘create_project’ or ‘edit_project’ are passed as GET variables or in the HTTP_REFERER then idc_add_upload_cap is called. This would of course require the user to be logged in.
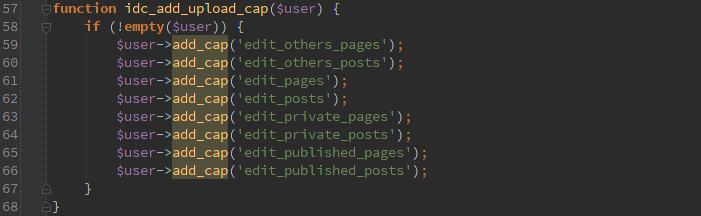
Look at all those fun capabilities we’ve got now. The capabilities will be removed by the idc_remove_upload_cap() function call if the variables aren’t passed.
Please developers, trust but verify!