Last week there was a vulnerability published for the WooCommerce Store Toolkit WordPress plugin from Visser Labs. I’ll often take a look at vulnerabilities and how they are resolved. In this case I noticed that the fix only covered one part and furthermore other plugin were vulnerable to similar issues. Kudos to Michael Visser for taking all these issues in stride and getting them resolved quickly.
The following plugins all had similar vulnerabilities that have been resolved.
- WooCommerce – Store Exporter < 1.8.4 (20,000+ active installs)
- WP e-Commerce – Store Toolkit < 2.0.2 (1,000+ active installs)
- Jigoshop – Store Toolkit < 1.3.9 (300+ active installs)
- WP e-Commerce – Store Exporter < 1.6.7 (1,000+ active installs)
- WooCommerce – Store Toolkit < 1.5.8 (5,000+ active installs)
WooCommerce – Store Exporter
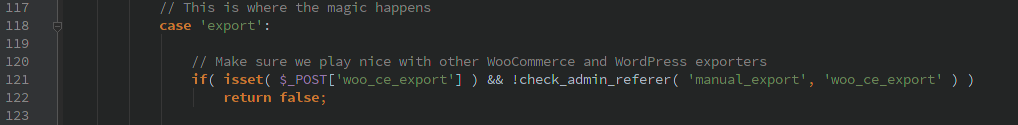
The most serious vulnerability is in this plugin. The woo_ce_admin_init() function is hooked by the ‘admin_init’ WordPress action (which happens when anything under the admin interface is loaded, not when an admin is logged in). The function checks the ‘action’ HTTP variable (GET or POST) and will perform many actions without further authorization.
The ‘export’ action does attempt to check a nonce but there is a small bug that renders it useless.
Because of the &&, if $_POST[‘woo_ce_export’] is never passed in then the nonce will not be checked. Which allows all kinds of fun stuff to be exported.
Timeline
- 2/8/2016 Original advisory posted
- 2/9/2016 Sent additional information
- 2/10/2016 Updated versions released