While sitting and waiting for my daughter at gymnastics several weeks ago I noticed an announcement for Ultimate Member plugin, sounded interesting so I bookmarked it to check out later.
Fast forward till last week when I noticed it sitting there and decided to take a look at it. I noticed a couple security issues and contacted the developers.
There were a few minor issues that they fixed, but the major ones are critical. If you are using this plugin, Update Immediately!
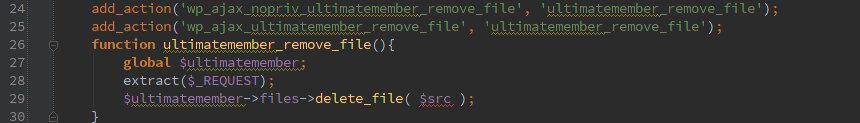
Delete any file
We’ve got an un-authenticated AJAX action to delete files here.
We definitely need some authorization on the user and/or the specific file to be deleted there when the AJAX call comes in.
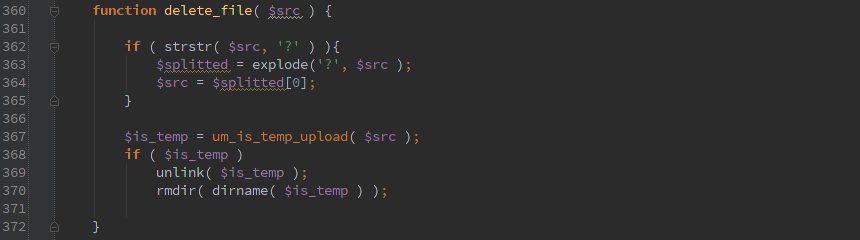
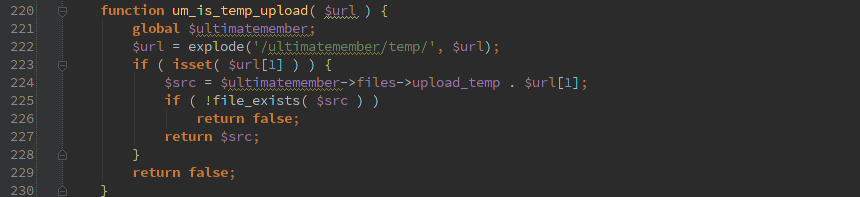
Well at least delete_file() is calling um_is_temp_upload() to make sure the file is a temporary file.
Uh-oh. It’s only pulling ‘/ultimatemember/temp/’ off the beginning. So it will happily take ‘../’ in the path and you can use it to delete any file that the user running php has permissions for.
Upload arbitrary files
Multiple issues all come together to make this especially evil.
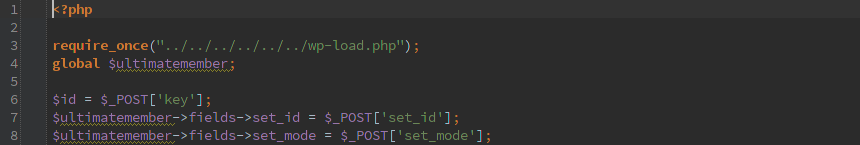 First off, the um-file-upload.php can be called directly and it bootstraps WordPress. I’d rather send every request through WordPress and not allow direct access to anything.
First off, the um-file-upload.php can be called directly and it bootstraps WordPress. I’d rather send every request through WordPress and not allow direct access to anything.
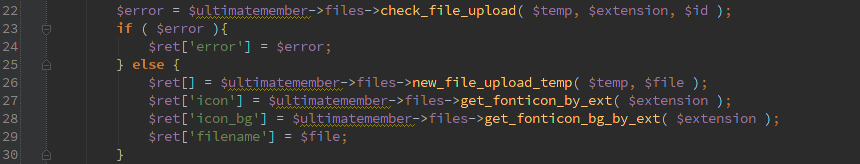
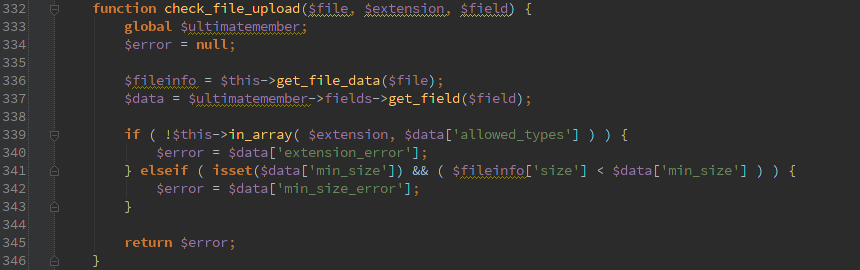
Then we call check_file_upload() and only move the file if it doesn’t return an error.
Cool, check_file_upload() at least checks for allowed extensions from an array. So if I try to upload something ending in .php it sets ‘$error = $data[‘extension_error’]; Here’s the rub, since user input is passed into check_file_upload(), get_field($field) call will return null if $field is some invalid field. So the end result is check_file_upload() is going to return null;
Now we’ve got a file uploaded and it even kicks back the full path that you need to call the file. Assuming the host will allow code execution from the uploads directory, you can now run code as the user running php.
Timeline
- 3/9/2015 Issues discovered
- 3/10/2015 Developer contacted
- 3/10/2015 Delete file issue fixed in Ultimate Member version 1.0.79
- 3/13/2015 Followup describing how the upload issue still worked
- 3/13/2015 Issue resolved in Ultimate Member version 1.0.84