Formidable Forms is a visual form builder WordPress plugin from Strategy 11. The free version has 200,000+ active installs which makes it one of the most popular contact form plugins for WordPress.
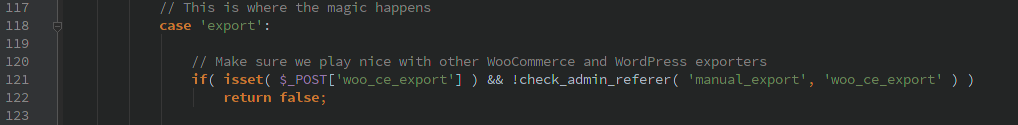
I noticed some potential security vulnerabilities in some of the more obscure AJAX actions they make available. Most of the actions are protected by a helpful function FrmAppHelper::permission_check() which checks if a user has the WordPress permission for the action as well as a valid nonce for the action. Kudos on implementing a system that makes it easy to be secure without duplicating code all over the place!
All of the actions uncovered require at least a valid WordPress account, but any account will work. If you are using this plugin, please update immediately.