Backup Guard is one of many WordPress plugins to designed to backup your site. The free version on wordpress.org claims to have 20,000+ active installs, there is no indication of how many installs the non-free version has. After disclosing this information the developer sent me a copy of the paid version, but I have not had time to investigate that code.
As of today, the included ChangeLog still does not have any release notes related to this version and I have not seen any announcements of any security issues.
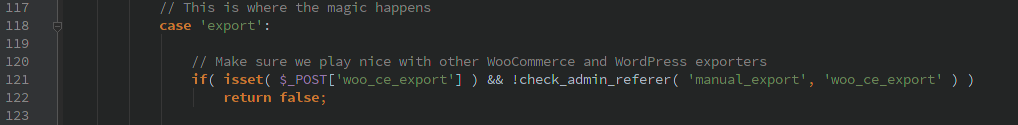
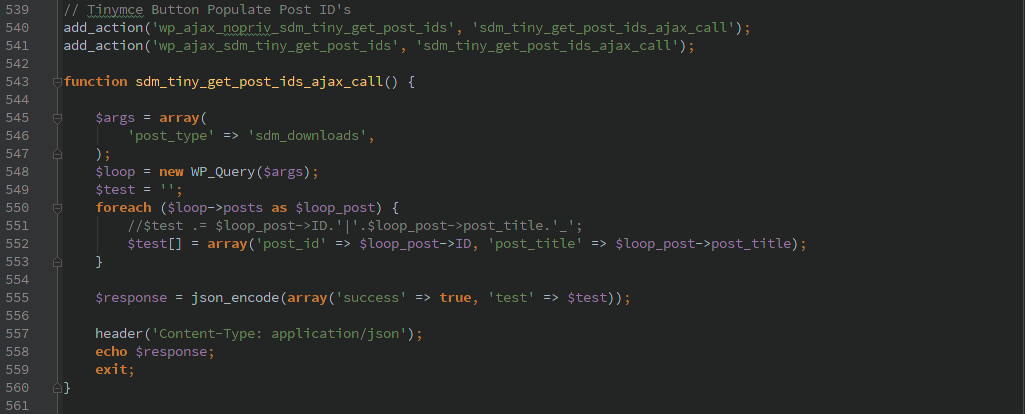
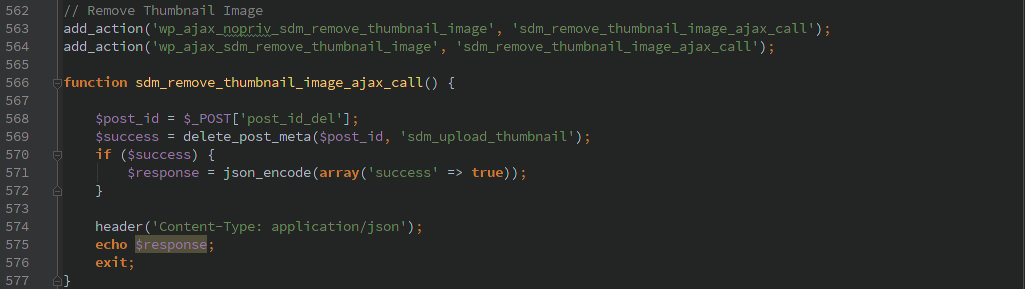
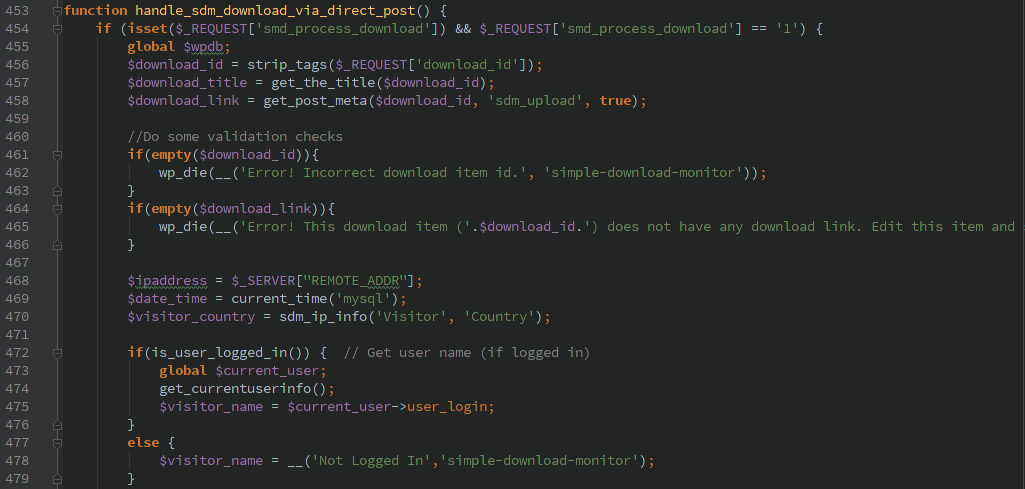
I noticed several issues related to their handling of AJAX requests. One of them allowed a non-authenticated user to trigger a manual backup. Though by default it uses .htaccess to keep anyone from accessing the backup files directly. With the paid version it might have been possible to pass in a remote location to backup the file to, but I did not have the code available when I did my initial analysis to determine if that was possible.
The other AJAX commands required a valid WordPress account (not just admin), none of the commands did any further authorization so a normal user could do any of the actions. There are lots of actions to choose from, the most interesting to me was ‘backup_guard_importBackup’.