The premium extension EDD Upload File for Easy Digital Downloads has a major security vulnerability in version 1.0.3 that was fixed in version 1.0.4. I’m not sure how many active installs there are of this plugin. If you are running version 1.0.3, upgrade immediately. This version allows someone to delete files, upload files, and potentially execute PHP code via those uploaded files.
As I’ve discussed previously, Easy Digital Downloads allows any WordPress action/filter that begins with ‘edd_’ to be called remotely and each function is supposed to do the authorization.
This gives us the opportunity to do two evil things in the EDD Upload File code.
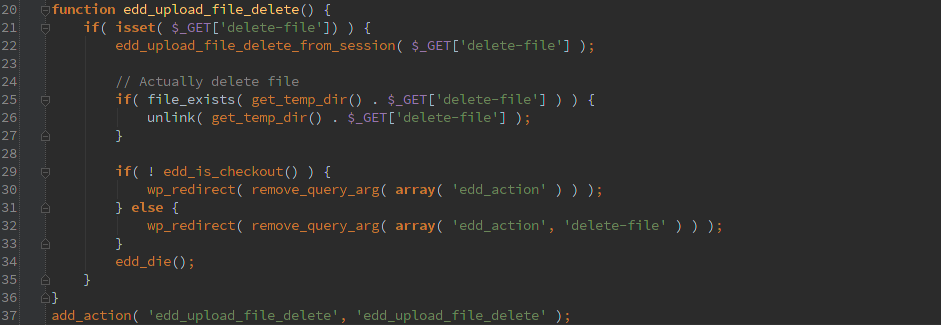
Delete any file
By calling GET ‘edd_action=upload_file_delete’ we get into this chunk of code and you can pass a ‘delete-file’ to specify a file to delete. The user running the PHP code would need appropriate permissions on the file in order to delete. The directory base is get_temp_dir() but you can use directory traversal to get out of there.
Upload arbitrary files
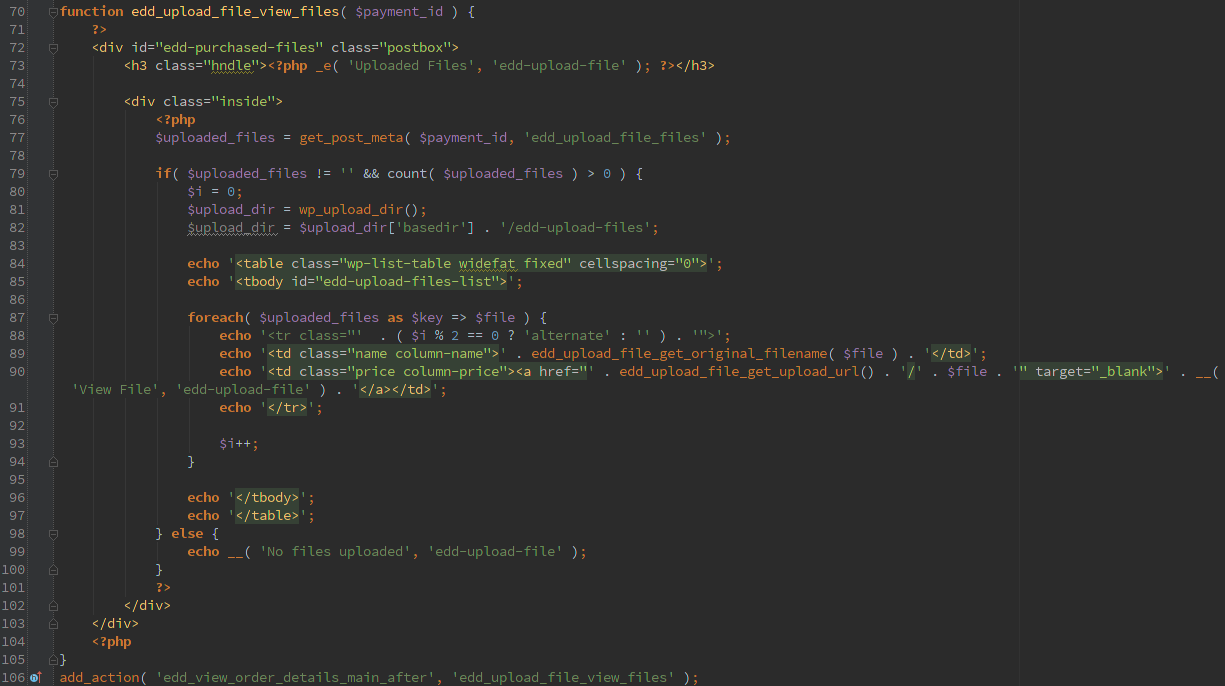 With the ‘edd_payment_receipt_before’ action we are able to upload arbitrary files. If the administrator setup extensions to allow then it would restrict files to be uploaded, but by default there isn’t any setup.
With the ‘edd_payment_receipt_before’ action we are able to upload arbitrary files. If the administrator setup extensions to allow then it would restrict files to be uploaded, but by default there isn’t any setup.
The files are renamed with a unique filename, presumably to eliminate conflicting filenames but also for a bit of security. Unfortunately, it uses uniqid() which isn’t very secure especially if we know the time the upload happens (or close enough).
Guessing the filename uploaded with uniqid() would be pretty easy, but in this version you don’t even have to do that because of another bug.
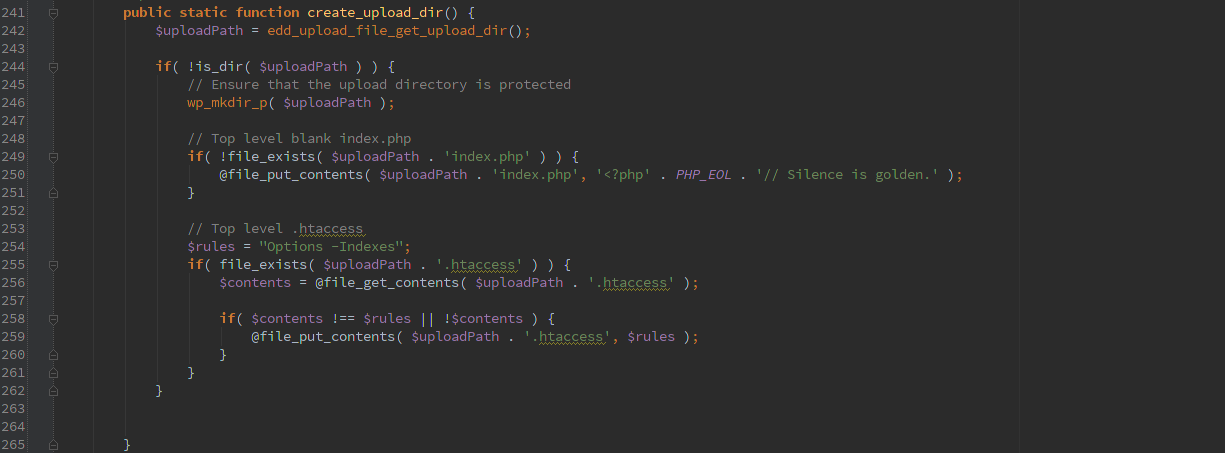
The code always checks to make sure the upload directory exists and if not it creates it as well as inserting a ‘index.php’ and ‘.htaccess’ to try to keep the webserver from listing the directory contents. Unfortunately in this case it is missing a ‘/’ so the index.php created would be something like ‘wp-content/uploads/edd-upload-filesindex.php’.
As I always recommend it is wise to keep your webserver from allowing directory listings in these directories as well as executing php/cgi from the uploads directory. In a default configuration it is trivial for someone to upload arbitrary php files and execute them remotely without any authorization.
Timeline
- 2/26/2015 1:12am Initial disclosure
- 2/26/2015 1:39am Developer response
- 3/17/2015 Updated version released